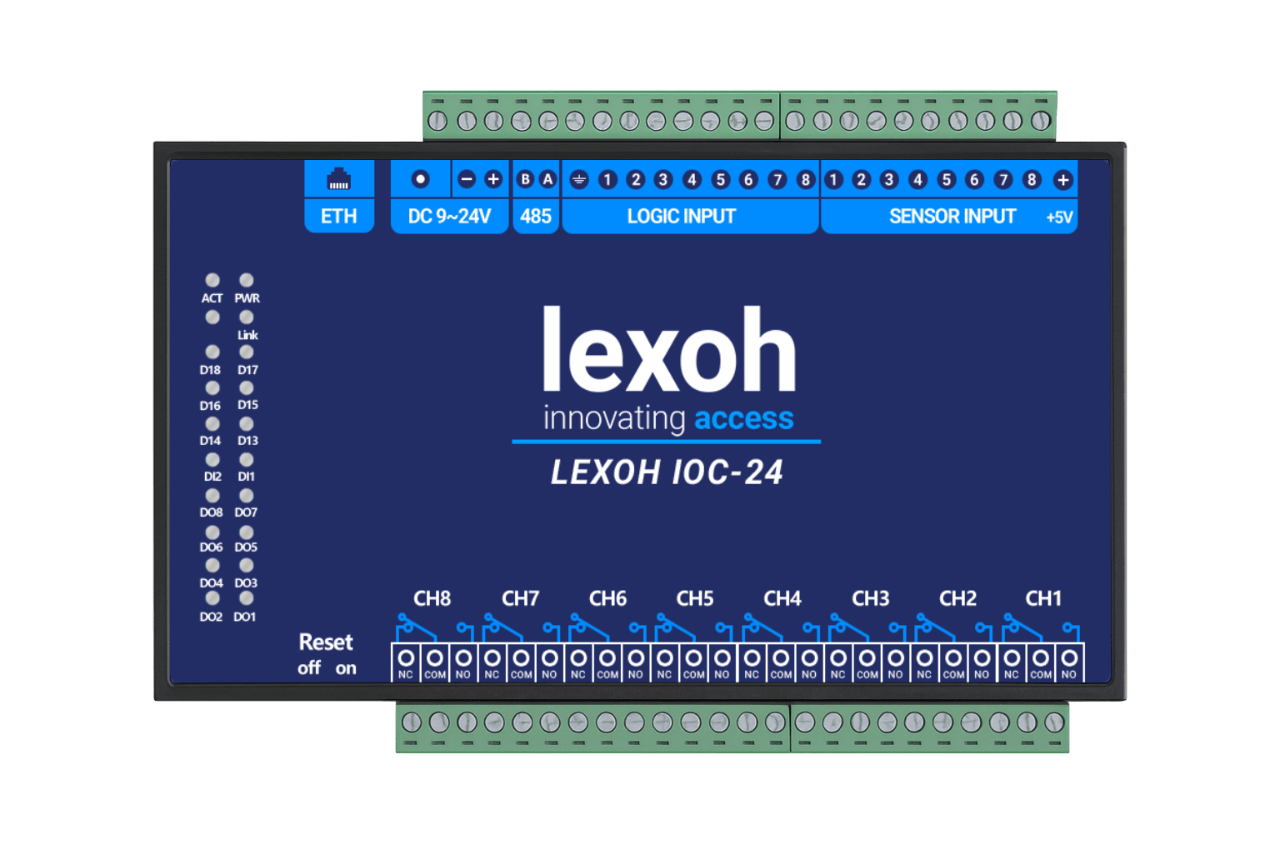
LDAP Authentication
Configure LDAP (Lightweight Directory Access Protocol) authentication to integrate LEXOH with your organization's existing user directory. This allows centralized user management and single sign-on capabilities. Access these settings through Settings → LDAP in the admin dashboard.
What is LDAP?
LDAP is an industry-standard protocol for accessing and managing directory information services. It allows LEXOH to authenticate users against your organization's central directory (such as Active Directory, OpenLDAP, or other LDAP-compliant servers).
- Centralized user management
- No need to maintain separate user accounts in LEXOH
- Users authenticate with their existing corporate credentials
- Automatic synchronization with organizational changes
- Enhanced security through centralized policies
Server Configuration
Configure the connection settings to your LDAP server.
Server Hostname
The IP address or hostname of your LDAP server.
ldap.company.local
192.168.1.100
Server Port
The port number on which the LDAP server is listening.
- 389 - Default LDAP port (unencrypted)
- 636 - LDAPS port (SSL/TLS encrypted)
- 3268 - Global Catalog (Active Directory)
- 3269 - Global Catalog SSL (Active Directory)
Secure LDAP (LDAPS)
Enable this option to use LDAP over SSL/TLS for encrypted communication with the LDAP server.
- Valid SSL certificate installed on LDAP server
- Certificate authority (CA) trusted by LEXOH server
- Port 636 accessible through firewall
LDAP Distinguished Names
The Distinguished Name (DN) specifies the location in the LDAP directory tree where user searches should begin.
What is a Distinguished Name?
A Distinguished Name (DN) is a unique identifier for an entry in an LDAP directory. It specifies the path to the entry in the directory tree hierarchy.
ou=users,dc=company,dc=local
cn=Users,dc=contoso,dc=com
DN Components
Distinguished Names are composed of several components:
Contact your IT administrator or use LDAP browser tools to discover the correct DN for your organization. Common tools include:
- Apache Directory Studio - Free LDAP browser and directory client
- LDAP Admin - Windows-based LDAP administration tool
- ldapsearch - Command-line tool (Linux/Unix)
How LDAP Authentication Works
Understanding the authentication flow helps troubleshoot connection issues.
- User Login Attempt: User enters their username and password in LEXOH login form
- LDAP Connection: LEXOH connects to the LDAP server using the configured hostname and port
- User Search: System searches for the user in the directory using the base DN
- Authentication: If user is found, LEXOH attempts to bind (authenticate) using the provided credentials
- Success/Failure: If authentication succeeds, user is granted access; otherwise, login fails
- Session Creation: On success, LEXOH creates a session and the user is logged in
Configuration Examples
Common LDAP configuration examples for different directory services.
Microsoft Active Directory
Server Port: 389 (or 636 for LDAPS)
Secure LDAP (LDAPS): Enabled (recommended)
Base DN: dc=company,dc=local
Alternative for specific OU:
Base DN: ou=Employees,dc=company,dc=local
OpenLDAP
Server Port: 389 (or 636 for LDAPS)
Secure LDAP (LDAPS): Enabled (recommended)
Base DN: ou=people,dc=example,dc=com
Azure Active Directory Domain Services
Server Port: 636 (LDAPS required for Azure AD)
Secure LDAP (LDAPS): Enabled (required)
Base DN: dc=contoso,dc=onmicrosoft,dc=com
Testing Your LDAP Connection
After configuring your LDAP settings, it's important to test the connection to ensure everything is working correctly.
Testing Procedure
- Save your LDAP configuration settings
- Log out of the admin account
- Attempt to log in using an LDAP user's credentials
- Verify successful authentication and access
- User can log in with their directory username and password
- No error messages appear during login
- User's name and information appears correctly in LEXOH
- Appropriate permissions are assigned based on user's directory groups
Troubleshooting Common Issues
Solutions to common LDAP configuration problems.
❌ Cannot Connect to LDAP Server
Symptoms: Connection timeout or "Connection refused" errors
Solutions:
- Verify the server hostname is correct and reachable from the LEXOH server
- Check that the port number is correct (389 for LDAP, 636 for LDAPS)
- Ensure firewall rules allow traffic on the LDAP port
- Test network connectivity using
pingortelnet - Verify the LDAP service is running on the server
❌ Authentication Failed
Symptoms: Login fails with valid credentials
Solutions:
- Verify the Base DN is correct for your directory structure
- Check that the username format matches your LDAP configuration (e.g., username vs. username@domain.com)
- Ensure the user account exists in the specified DN path
- Verify the user account is enabled and not locked
- Check for special characters in username or password that may need escaping
❌ SSL/TLS Certificate Errors
Symptoms: "Certificate verification failed" or "SSL handshake failed" errors
Solutions:
- Ensure the LDAP server's SSL certificate is valid and not expired
- Import the certificate authority (CA) certificate to the LEXOH server's trusted certificate store
- Verify the certificate hostname matches the server hostname in configuration
- Check that port 636 is being used for LDAPS connections
- For testing only: Temporarily disable certificate verification (not recommended for production)
❌ User Not Found in Directory
Symptoms: "User not found" or "Invalid username" errors
Solutions:
- Verify the Base DN includes the organizational unit where users are located
- Check that the user search scope is configured correctly (typically subtree search)
- Use an LDAP browser tool to verify the user exists at the expected location
- Ensure the username attribute matches your directory (e.g., sAMAccountName, uid, cn)
- Check that the LEXOH service account has permission to search the directory
Security Best Practices
Follow these security recommendations when configuring LDAP authentication.
Essential Security Measures
- Always use LDAPS: Enable Secure LDAP to encrypt credentials during transmission
- Valid certificates: Use properly signed SSL certificates from trusted certificate authorities
- Restricted bind account: If using a bind account, grant it minimal read-only permissions
- Network segmentation: Place LDAP servers on secure network segments with strict firewall rules
- Monitor authentication: Enable logging and monitor for failed authentication attempts
- Regular updates: Keep LDAP server software and LEXOH platform up to date with security patches
Never use unencrypted LDAP (port 389) without SSL/TLS in production environments. Credentials will be transmitted in plain text and can be intercepted by attackers. Always configure LDAPS (port 636) with valid SSL certificates.
📚 Additional Resources
Ready to Configure LDAP?
Continue setting up your user authentication system. Configure user roles and explore system settings.